On April 13, 2020, the Cyberspace Administration of China (“CAC”), together with eleven other government authorities (including without limitation Ministry of Industry and Information Technology, Ministry of Commerce, Ministry of Public Security, National Development and Reform Commission, and State Administration for Market Regulation) jointly released the Measures on Cybersecurity Review (the “Measures”). This regulation will take effect on June 1, 2020, repealing simultaneously the Measures on the Security Review of Network Products and Services (Trial) (“Trial Measures”) implemented on June 1, 2017. Additionally, following the enactment of the Measures, CAC held a press conference (the “Q&A”) to answer the relevant questions and thus provide more guidance on this upcoming regulation.
The Measures follows the requirement of cybersecurity review under the existing Trial Measures, and further provides and elaborates the applicable scope, procedure and factors of cybersecurity review. This enhanced regulation has further indicated that China decides to keep strengthening the IT supply chain to ensure the security from the national level. As such, companies are advised to understand the legal implication and compliance requirement when dealing with the procurement or supply of IT products or services.
1、Overview
A. Purpose of the Measures
The cybersecurity review system is formulated in light of the requirements under the PRC National Security Law and the PRC Cybersecurity Law (“CSL”), as article 59 [1] of the former and article 35 [2] of the latter respectively require national security review on key technologies and network information technology products and services that affect or may affect State security and any purchase of network products and services by the operator of critical information infrastructure that may threaten the national security. As such, per the Q&A, in consideration of the importance of critical information infrastructure (“CII”) to national security, the cybersecurity review is aimed to ensure the security of CII supply chain.
B. Applicable Scope of the Measures
a)Who are Subject to the Cybersecurity Review?
The Measures, in line with the CSL, specifies that any purchase of network products and services by critical information infrastructure operators (the “CIIO”) that may impact national security will be subject to the cybersecurity review. Moreover, the Measures further clarifies that, such CIIO refer to those operators determined by the competent authorities (such as Ministry of Industry and Information Technology) for CII protection. That means, generally, a network operator is not obligated to apply for security review, unless it is determined by competent authorities.
Notably, according to the Q&A, operators of critical network and information system in certain sectors and industries, such as telecommunications, radio and television, energy, finance, road and water transportation, railways, civil aviation, postal services, water conservancy, emergency management, healthcare, social security, national defense-related science and technology, shall consider applying for cybersecurity review when purchasing network products and services. Therefore, enterprises in the above industries and sectors are suggested to pay attention to the cybersecurity review as well, even they are not determined as CIIO by authorities.
b)What Kind of Network Products and Services Will be Reviewed?
According to the Measures, the term “network products and services” mainly refers to core network equipment; high-performance computers and servers; large-capacity storage devices; large-capacity databases and application software; network security equipment; cloud computing services; and other network products and services that have a significant impact on CII security.
In light of the above description, not all network products and services are subject to the cybersecurity review. However, the description leaves room for discretion by authorities. Besides, it is noteworthy that, for network products or services that fall into the abovementioned categories, only when the purchase may impact national security as prejudged by the CIIO will be subject to the cybersecurity review. As provided in theMeasures, the guidelines for pre-judgment will be formulated by CII protection sectoral authorities.
c)Who is Responsible for Conducting the Cybersecurity Review?
Compared with the Trial Measures, the Measures removes the participation of third-party cybersecurity examination agencies, and clarifies that the Cybersecurity Review Office (“CRO”) of CAC is responsible for the receipt of cybersecurity review applications and the preliminary review; and the specific work will be done by China Cybersecurity Review Technology and Certification Center. Besides, comments from the members of the cybersecurity review working mechanism and the relevant CII protection authorities will be solicited by the CRO as well.
2、Legal Implications of the Measures from the Perspective of Purchasers
A. Impact on Procurement Schedule
a)When to Apply for Cybersecurity Review?
Generally speaking, a purchaser shall apply for a cybersecurity review prior to the execution of a contract with a product or service provider. As suggested by CAC during the Q&A, if a purchaser apply for review after signing the contract, it is recommended to indicate that the contract shall only be effective after the cybersecurity review procedure is completed, in order to avoid losses resulting from the failure of passing the cybersecurity review.
b)How Long Does the Cybersecurity Review Take?
The cybersecurity review generally takes 55 working days: 10 working days to determine whether a cybersecurity review is necessary, 30 working days for the preliminary review by the CRO of CAC and another 15 working days for the members of cybersecurity review working mechanism and relevant CII protection authorities to provide comments on CRO’s suggested finding of the review. In complicated cases, the aforesaid time of preliminary review can be extended by 15 working days. Notably, where the CRO requires submission of supplementary materials, the period of preparation and submission of supplementary materials shall not be included in the aforementioned time limits of review.
If a unanimous agreement is reached by the members of the cybersecurity review working mechanism and relevant CII protection authorities on the suggested finding , the review will be completed; otherwise, the review will enter into a special process, the time limit of which is 45 working days and can be extended further if necessary.
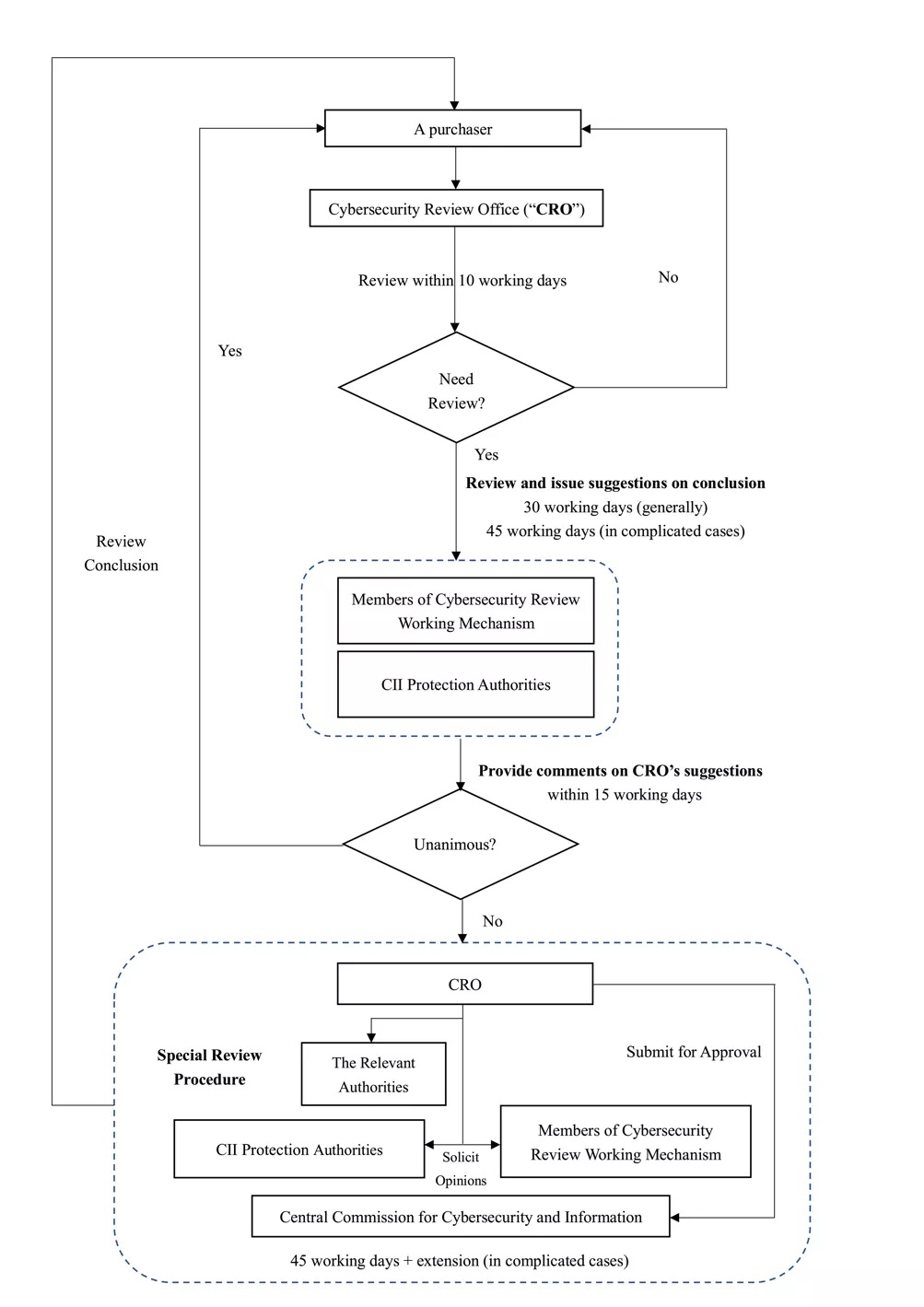
As such, relevant enterprises obliged to apply for a cybersecurity review may have to take the review into account and re-consider the time schedule for procurement, especially when the procurement is managed by global headquarter overseas.
B. Impact on Procurement Procedure
Due to the requirement of the cybersecurity review, enterprises may have to establish an operation procedure to prejudge the necessity of review when purchasing network products and services, and prepare for the application for the cybersecurity review if needed.
As provided under the Measures, to apply for a cybersecurity review, the following materials shall be submitted:
-
a letter of application;
-
an analysis report concerning the impact or possible impact on national security;
-
the procurement document, agreement, contract to be concluded; and
-
other materials required for the cybersecurity review.
The guidelines for pre-judgement and the templates of the above materials have not been issued yet, so the relevant enterprises are suggested to pay close attention in this regard.
C. Impact on Procurement Contract
As aforementioned, the contracting parties, especially the purchaser, shall fully understand and consider the potential consequence of failing to pass the cybersecurity review. Specifically, to mitigate the risks therein, it is advisable for the purchaser to make it clear in a contract or an agreement at least that:
-
the product and/or service provider is obliged to cooperate in the cybersecurity review by making commitments not to take advantage of the provision of the product and/or service to illegally obtain user data, illegally control and manipulate user equipment, and not to suspend product supply or necessary technical support services without justifiable reasons;
-
the procurement contract or the relevant provisions shall only be effective after the procurement of the product and/or service has passed the cybersecurity review; and
-
the contractual liabilities and obligations of the parties when the product and/or service fail to pass the cybersecurity review.
D. Legal Liabilities
Failure to apply for the cybersecurity review may incur administrative punishments under theCSL. Specifically, once the CIIO who uses products or services that have not undergone or failed the cybersecurity review, it will face the following legal consequences: (1) be ordered by the competent authority to stop such use, and (2) be subject to a fine equivalent to more than 1 but less than 10 times the purchase price, and (3) the person directly in charge and other directly liable persons shall be subject to a fine of ranging from RMB10,000 (about USD1,407) to RMB100,000 (about USD14,072).
3、Legal Implications of the Measures from the Perspective of Vendors
A. Higher Requirements for the Quality of Network Products and Services
Pursuant to the Measures, the cybersecurity review will focus on the potential risks to national security caused by network products or services, thereby a vendor of network products and services may have to face higher security requirements in consideration of the following factors to be considered in the review:
-
risk of the CII being illegally controlled or subject to interference or destruction by the use of the product or service, or the theft, leakage, or damage of important data;
-
the damages to the continuity of CII operations caused by a disruption in the supply of the product or service;
-
the safety, openness, transparency, source diversity, and reliability of supply channels regarding the product or service, as well as the risk of supply disruption due to political, diplomatic, trade, or other reasons;
-
the product or service provider’s compliance with Chinese laws, administrative regulations, and departmental rules; and
-
other factors that may jeopardize the security of CII and national security.
B. Obligation of Cooperation in the Cybersecurity Review
As mentioned above, when selling network products or services to CII operators, a vendor may be required to cooperate in the cybersecurity review and make the relevant commitments as required. Therefore, it is suggested that vendors pay close attention to the fulfillment of relevant obligations in order to avoid the potential liabilities for breach of contract.
C.Impact on Procurement Contract
Due to the aforementioned obligation of cooperation, vendors may be required to provide relevant materials for the cybersecurity review. As such, it is suggest to clarify the obligation of confidentiality and the scope of authorization in the contract or agreement when providing materials, so as to avoid the potential improper disclosure of trade secrets or unauthorized use of intellectual property rights in the course of the cybersecurity review.
4、Conclusion
In view of the increasing complicated global trend of trade, China is strengthening national security protection in cyberspace. For CIIO, it is highly necessary to establish a mechanism for cybersecurity review before the effective date of the Measures to avoid the potential legal and compliance risks; and for those network operators in certain important industries and sectors, they are recommended to consider the cybersecurity review as required. Meanwhile, it is advisable to keep close eye on the issue of the relevant guidelines and templates as well.
Besides, the enterprises, as network products and services providers, are advised to pay attention to the quality of products and services, as well as the obligations in the cybersecurity review when selling products or services to CIIO.
References
[1] Article 59 of the National Security Law stipulates that “The State shall establish a review and regulation system and mechanism for State security, and carry out State security review against foreign investment, specific items and key technologies and network information technology products and services that affect or may affect State security, projects relating to State security matters and other material matters and events in order to effectively prevent and resolve State security risks”.
[2] Article 35 of the Cybersecurity Law stipulates that “Any purchase of network products and services by the operator of critical information infrastructure that may threaten the national security is subject to the national security review conducted by the CAC together with competent departments of the State Council”.


